The question of whether faxing is more secure than email has been debated for decades. The answer to this question is not black and white, and largely depends on the nature of your work, the type of sensitive information that you are exchanging, the level of sophistication of the people that are trying to attack your network, and how well you have secured your system.
The debate can be narrowed down into two camps: those who believe that faxing is less prone to interception by hackers because it sends data over a physical line versus those who believe that hacking isn’t an issue with fax machines since they don’t connect directly to networks or send their transmissions over an internet connection like email does. There are plenty of reasons why each camp may be right or wrong. Let’s examine the claims of those who think that faxing is more secure than email.
Security aspects of faxing vs email
Security aspects of faxing
Security aspects of email
The physical aspect
Accessibility
The overarching characteristic of fax compare to email is simple: it’s physical . All data sent via fax uses a telephone line, which means that hackers have to have access to your phone lines in order to tap in. They have to have physical access in order to intercept information being sent via fax. On the other hand, motivated hackers can intercept emails that are traveling over an internet connection without having to come into direct contact with your network or system.
Once a hacker has physical access, they still need time and expertise to wire-tap phone lines effectively. The most sophisticated hackers have the ability to tap into phone lines and intercept data being sent or received. Doing a phone tap requires a specific device and takes time to set up. And given the current sophistication of hackers, breaking into a phone line for interception purposes would be considered advanced hacking.
However, the physical aspect opens up other risks. For example, in some businesses the fax machine might located in a public area where other employees have access to it. A third person could see or steal a message that arrived and wasn’t collected in time. This is not likely to occur with email, where messages arrive in typically password-protected computers and/or reside on secured email servers.
The software aspect
Fax machines aren’t susceptible to computer-based malware. This means that they are more secure from this attack vector, but there are still risks that you have to mitigate.
Viruses
A fax machine is a closed, hardware-based system. Hence, you can’t install any kind of computer virus or malware on an analog fax machine. This makes traditional fax machines incapable of transmitting viruses over the phone lines, meaning that a sender won’t be able to transmit viruses to the recipient through a fax machine either.
Malware
While it may be possible to create malware that attacks fax machines, and especially high-end, internet-fax-capable multifunction devices that are effectively large computers, plain old fax machines are currently not known to be a viable attack vector. It is much more worthwhile for malware authors to target computers and smartphones than fax machines.
Encryption
We frequently come across the question, “are fax machines encrypted?”.
When you send a fax on a regular fax machine that you bought at your local office supplies store or on Amazon, the transmitted fax is not encrypted. It is sent in a well-known digital transmission format called ITU-T fax group 3 or 4 (formerly CCITT fax group 3 or 4) and can be intercepted and read by anyone who has the ability to tap into your phone line.
There do exist solutions to encrypt fax transmissions, for example, as used by diplomatic missions and high-security institutions. However, these require dedicated mutually-compatible equipment on both the sending and the receiving ends. Therefore, we can’t generalize from them to what might be typical fax usage..
It’s important to note that when online fax service providers claim to offer encrypted fax, as some appear to do in the Google search results below, they’re not referring to the actual fax transmission. Instead, they might be referring to: their file storage, access to their systems, or the security of conveying of fax messages by email or API before and after their transmission and reception as faxes.
The fax service provider which appears as a first result in Google for the search term “encrypted fax” confirms this by saying:
The security of messages sent through the InterFAX system may be enhanced by encrypting your emails. While this will NOT encrypt the fax transmission from our servers to the fax machine itself, it WILL secure the contents of your message while it is in transit from your computer to our servers.
upland InterFAX
In practical terms, neither are most emails encrypted, even though the capability to sign and encrypt emails has existed for a long time and is available on most modern email clients.
Mitigating this lack, however, is the fact that most email servers today “speak” TLS between them, effectively making eavesdropping and tampering of email transmissions impossible.
The human factor
Phishing
Attackers prefer email over fax machines as they are less immediately susceptible to phishing. For malicious hackers, the advantage of email over faxes is that they can achieve their objective by tricking a user into opening a dangerous attachment.
In this sense, it’s easier for attackers to use email to infect users with malware. However, unlike email, fax machines do not have a mailbox where they can collect messages from the outside world. And even if they are stored electronically, incoming faxes have to be manually transferred into storage by someone who knows what they are doing. You could consider this as an additional layer of protection against attacks and threats.
Spoofing
Email spoofing is a technique where attackers change the “from” field of an email message to make it appear as though it came from someone else. Usually, this is used for criminal purposes such as fraud or phishing. This can be mitigated, but depends on the spoofed party to set up their email servers (more specifically, their DNS servers) correctly.
Similarly, spoofing is also possible when faxing. In the context of faxing, spoofing can mean two things:
- Sending a fax header (CSID) that pretends to show a sender other than the actual sender.
- Sending a fax with a fake caller ID. This requires deeper access to telephony settings, so we’ll
Fax header (CSID) spoofing
A fax can be set to send a header to the receiving party. The header is a long piece of text that can include anything, but usually shows the sending date and time, the fax number from which the fax was sent, the sender name, and other information. This is how a Canon user manual presents it:
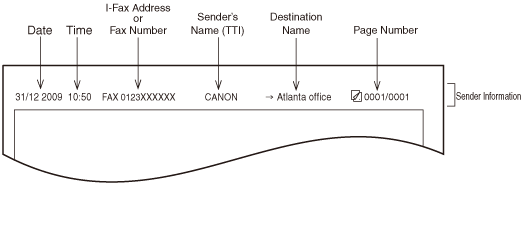
The sender fax number and name, which might be relied upon by the fax recipient to verify the veracity of the fax, are quite simple to change on the sending fax machine through its regular settings.
Forging
Forging the contents of both emails and faxes is quite simple. But while faxes provide relatively few clues about their senders, emails provide a plethora of information about the path they took to arrive. And even if an email can’t be said to have been forged, frequently the reputation of its sender can give a hint as to its possibility of being real.
Forging a fax is a simple exercise in any image editor. Gaining access to any company’s letterhead is easily done through the internet and all that’s left is to fill in the details. People’s trust in accepting faxed documents for their signatures is in this sense quite naive. Once this is done, it’s again quite easy to set a fax machine’s setting to do the appropriate fax header spoofing described above. This leaves the recipient with little information to guide their decision as to whether a document is real or fake, aside from common sense.
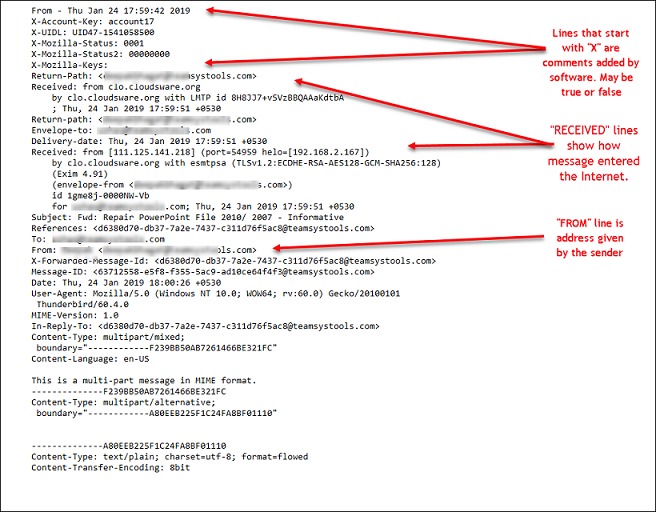
In a sense, forging an email is just as simple. But at least when an email arrives, it carries a large quantity of metadata which allows its analysis, as the following image from shows.
In conclusion
As you can see, there’s really no way to say whether faxing is more or less secure than email when both options are open to attack. The truth is that it all depends on the specific nature of your work and the risks that you face since these two methods of communication don’t create a different threat.
